DPA – 2020
Version: January 1, 2020
1. Background
This Data Processing Agreement (“Data Processing Agreement”) applies to the processing by Bringg Delivery Technologies Ltd., of 1 Habarzel Street, Tel Aviv 6971001, Israel (“Bringg”), of Personal Data (as defined below) on Customer’s behalf as a Data Processor for the provision of those Services described on a Service Order (the “Services”) entered into between Customer (“Data Controller”) and Bringg (“Data Processor”) (this Data Processing Agreement, together with the Service Order and the Terms of Service incorporated by reference into the Service Order, the “Services Agreement”). Data Controller and Data Processor are collectively referred to as the “Parties”, and each a “Party”.
This Data Processing Agreement applies only to the extent that the EU 2016/679 General Data Protection Regulation (GDPR) applies to the processing by Bringg of Personal Data as part of the Services offered by Bringg under the Services Agreement. In all other circumstances this Data Processing Agreement is not valid and is not legally binding.
Unless otherwise expressly stated in the Service Order, this version of the Data Processing Agreement shall be effective and remain in force for the term of such Service Order. In the event there is any conflict or inconsistency between the terms of this Data Processing Agreement and the terms of the Service Order, the terms of the Service Order shall control. In the event there is any conflict or inconsistency between the terms of this Data Processing Agreement and the terms of the online Terms of Service, the terms of this Data Processing Agreement shall control.
When providing the Services, the Data Processor may collect, process, transfer and gain access to personal data of such individuals on behalf of the Data Controller for the purposes of rendering the Services.
This Data Processing Agreement specifies the data protection obligations of the Parties. It applies to all activities performed by the Data Processor for Data Controller in connection with the Services in the course of which the Data Processor, its staff or a third party acting on behalf of Data Processor receive access to personal data of individuals.
It is hereby agreed that Data Processor may store the Personal Data on cloud services such as Amazon Web Services and Google Cloud only located within the European Union and may allow its employees to access the Personal Data, all in order to perform Data Processor’s obligations and duties under the Services Agreement.
It is agreed that a copy of this Data Processing Agreement may be forwarded to the relevant supervisory authority, if required under applicable law. Furthermore, the Parties agree that such authority has the right to conduct an audit of the Data Processor with respect to the subject matter of this Data Processing Agreement.
2. Data Processor’s Obligations
2.1 The Data Processor, and any person acting under its authority, will collect and process Personal Data (as defined below) under the Services Agreement, only on behalf of the Data Controller, during the Term and only for the purpose of fulfilling the Services Agreement, under which Bringg will provide the Data Controller access to its proprietary logistics and delivery management platform. Data Processor will carry out the data processing operations, including with regard to transfers of Personal Data to a third country or an international organisation, in accordance with this Data Processing Agreement and any documented instructions received from the Data Controller, unless Union or Member State Law to which the Data Processor is subject requires the Data Processor to act otherwise. In the later event, the Data Processor shall inform the Data Controller of that legal requirement before processing, unless that law prohibits such information on important grounds of public interest.
2.2 Personal data to which Data Processor may receive access to concern the Data Controller’s internal and/or external mobile personnel, end user customers, administrators, and/or any other individuals whose Personal Data is provided by the Data Controller to the Data Processor (“Data Subjects”).
2.3 The data processing activities will generally include the following categories of personal data (“Personal Data”): any information provided by the Data Controller to the Data Processor, which may include such end-users’ name, telephone number, address, e-mail address, list of delivered goods, etc.; such mobile personnel’s name, phone number, locations and email address, IP/MAC address.
2.4 The Data Processor will comply with applicable privacy laws and regulations while processing and using the Personal Data, including by implementing adequate measures to ensure the privacy of the Data Subjects’ personal data held by the Data Processor.
2.5 Other than as permitted under this Data Processing Agreement, the Data Processor will not disclose, make available or transfer the Personal Data to any third party. The Data Processor is not allowed to collect, process or use any Personal Data made available to it for any purposes other than for the performance of the Services Agreement. Copies or duplicates of any Personal Data made available hereunder may only be made with the approval of Data Controller.
2.6 Data Processor shall keep records of its processing activities in accordance with applicable law and will grant to Data Controller and its designees all required information and access rights, strictly in accordance with the Data Processor’s security policy, in order to demonstrate and verify Data Processor’s compliance with the Services Agreement, this Data Processing Agreement and with applicable data protection law. The Data Processor shall allow for and contribute to audits, including inspections, conducted by the Data Controller or another auditor mandated by the Data Controller at the Data Controller’s sole expense. If and to the extent Data Controller engages third parties to conduct the audit, such third parties have to be bound to confidentiality obligations similar to those agreed by Data Processor under this Data Processing Agreement. Notwithstanding the above, the Data Controller shall only be entitled to conduct such inspection during business hours and no more than once during one calendar year, provided that nothing in this section shall limit the timing and scope of any audit required to be conducted by applicable privacy law.
2.7 Data Controller shall provide the Data Processor reasonable prior written notice of any audit or inspection to be conducted under this section and shall make (and ensure that each of its auditors makes) reasonable endeavours to avoid causing (or, if it cannot avoid, to minimize) any damage, injury or disruption to the Data Processors’ premises, equipment, personnel and business while its personnel are on those premises in the course of such audit or inspection.
2.8 Data Processor will notify Data Controller without undue delay if Data Processor is of the opinion that a written instruction received from Data Controller is in violation of applicable data protection law and/or in violation of contractual duties under the Services Agreement.
2.9 Data Processor will notify Data Controller without undue delay if Data Processor or Data Processor’s employees violate the provisions of this Data Processing Agreement. Furthermore, if Data Processor is of the opinion that Personal Data have been or might have been illegally transferred or otherwise illegally disclosed by it to a third party, Data Processor will notify Data Controller thereof without undue delay. In case of any loss of or unauthorized access to Personal Data stored by Data Processor, Data Processor will inform Data Controller promptly and assist Data Controller promptly in fulfilling its statutory obligations under applicable data protection and IT security laws.
2.10 The Data Controller hereby grants the Data Processor a general authorization to engage sub-processors for the purpose of providing the Services under the Services Agreement. Data Processor will, with respect to sub-processors who have access to personal information provided by Data Controller: (i) communicate the name, address and contact details of the subcontractor(s) and the tasks of the subcontractor(s) prior to engaging the subcontractor, (ii) ensure that it has in place or conclude prior to engaging the subcontractor a sub-processing agreement between Data Processor and the subcontractor that is no less protective with respect to Data Controller’s interest and protection of Personal Data than required by applicable law, and in particular providing sufficient guarantees to implement appropriate technical and organisational measures in such a manner that the processing will meet the requirements of applicable law, (iii) ensure that an adequate level of data protection for subcontractors that are located outside of the EU/EEA exists or is created (e.g. by using subcontractors that are certified under the EU/U.S. Privacy Shield or by concluding EU Standard Contractual Clauses), (iv) ensure that it has sufficient rights against the subcontractor to enforce a claim or request of Data Controller in context of the Services provided by the subcontractor; and (v) provide copies of documentation evidencing (ii) to (iv) above prior to engaging the subcontractor, if requested by the Data Controller. Data Processor is obliged to inform Data Controller of any intended changes concerning the addition or replacement of a subcontractor in writing or by email without undue delay and give the Data Controller the opportunity to object to such changes. Upon Data Controller’s request, Data Processor is obliged to provide Data Controller with an updated list of subcontractors being at that time subcontracted by Data Processor with respect to personal information received from Data Controller without undue delay.
2.11 Data Processor will ensure that its personnel authorised to process the Personal Data on its behalf, will keep confidential and will not make available any Personal Data received in connection with the Services Agreement to any third party.
2.12 Data Processor will implement adequate technical and organizational measures to ensure security of its network and data centre operations for the purposes of providing the Services to Data Controller in accordance with Exhibit 1.
2.13 Data Processor undertakes to use reasonable endeavours to fully cooperate and to comply with any instructions, guidelines and orders received from the relevant supervisory authority.
2.14 Where applicable, Data Processor shall, taking into account the nature of the processing and the information available to the Data Processor, assist Data Controller in meeting the Data Controller’s obligations to Data Subjects pursuant to applicable law, including assistance in helping Data Subjects to exercise their rights under applicable law, by implementing appropriate technical and organisational measures.
2.15 Upon termination of the Services Agreement, Data Processor will, at the choice of the Data Controller, delete or return to the Data Controller, all Personal Data provided by Data Controller during the provision of the Services, and delete existing copies of such Personal Data which are kept in its systems and/or premises, all unless Union or Member State Law requires storage of the Personal Data by the Data Processor. Return or deletion of the Personal Data may be made by way of an application program interface made available to the Data Controller. In that case, the Data Processor warrants that it will guarantee the confidentiality of the Personal Data transferred and will not actively process the Personal Data transferred anymore.
2.16 The Data Processor shall notify the Data Controller without undue delay after becoming aware of a Personal Data breach.
2.17 To the extent required under applicable data protection law, the Data Processor shall employ a data protection officer and appoint (in writing) a representative within the European Union.
3. Obligations of Data Controller
2.1 Data Controller is responsible for the evaluation of the admissibility of the data processing activities and for ensuring the rights of the Data Subjects concerned.
2.2 Data Controller shall be entitled to issue written instructions regarding the scope and the procedure of the data processing activities, within the scope of the Services Agreement. Data Processor may charge applicable fees for such instructions or terminate the Services Agreement if it does not wish to comply with such instructions.
2.3 The Data Controller warrants and undertakes that: (i) the Personal Data has been collected, processed and transferred in accordance with the laws applicable to the Data Controller, including if required by applicable law, the Data Controller has received all required consents from its data subjects; (ii) it will provide the Data Processor, when so requested, with copies of relevant data protection laws or references to them (where relevant, and not including legal advice) of the country in which the Data Controller is established; (iii) after assessment of the requirements of the applicable data protection law, the security measures that the Data Processor should implement under this Data Processing Agreement are appropriate to protect the Personal Data against accidental or unlawful destruction or accidental loss, alteration, unauthorised disclosure or access, in particular where the processing involves the transmission of data over a network, and against all other unlawful forms of processing, and that these measures ensure a level of security appropriate to the risks presented by the processing and the nature of the Personal Data to be protected having regard to the state of the art and the cost of their implementation; (iv) it will promptly respond to any inquiries from Data Subjects and the applicable authorities concerning processing of the Personal Data by the Data Processor; (v) to ensure the rights of the Data Subjects concerned, including without limitation to enable the Data Subjects to inspect and correct the Personal Data which is held by the Data Processor where such Personal Data is inaccurate, incomplete, unclear, outdated, all as required under applicable data protection laws; (vi) not provide to Data Processor any data of Data Subjects under the age of 16; and (vii) the Data Subject has been informed or will be informed before, or as soon as possible after, the transfer, that his/her personal data could be transmitted to a third country, outside of the EU.
2.4 Data Controller agrees to defend, indemnify and hold the Data Processor its officers, directors, employees, agents, vendors and third party providers, harmless against any and all claims, losses, penalties, causes of action, damages, liability, costs, expenses (including but not limited to attorney’s’ fees and costs) or claims caused by or resulting directly or indirectly from: (i) Data Controller’s breach of any representation, warranty or obligation under this Data Processing Agreement or under applicable privacy law which applies to the Data Controller; and; (ii) a third party claim, suit or proceeding that use of the Personal Data within the scope of this Data Processing Agreement infringes any privacy right of a third party.
4. Personnel
2.1 Data Processor will be responsible for using qualified personnel with data protection training to provide the data processing activities.
5. Technical and Organizational Measures
Data Processor will implement the technical and organizational security measures as stipulated in Exhibit 1 of this Data Protection Agreement. The technical and organizational security measures are aimed at protecting Personal Data against accidental or unlawful destruction or accidental loss, alteration, unauthorized disclosure or access and against all other unlawful forms of processing.
The Data Controller hereby acknowledges that after assessment of the requirements of the applicable data protection law, the security measures that the Data Processor should implement under Exhibit 1 of this Data Protection Agreement are appropriate to protect the Personal Data against accidental or unlawful destruction or accidental loss, alteration, unauthorised disclosure or access, and against all other unlawful forms of processing, and that these measures ensure a level of security appropriate to the risks presented by the processing and the nature of the Personal Data to be protected having regard to the state of the art and the cost of their implementation.
6. Term
This Data Processing Agreement shall become effective upon the effective date of the Services Agreement that expressly incorporates the terms of this Data Processing Agreement by reference (“Effective Date”). This Data Processing Agreement shall remain in full force until the Services Agreement terminates (the “Term“).
In the event that the Data Processor is in breach of its obligations under this Data Processing Agreement, then the Data Controller may temporarily suspend the transfer of Personal Data to the Data Processor until the breach is repaired or the Data Processing Agreement is terminated.
7. Miscellaneous
Each Party’s and all of its affiliates’ liability, taken together in the aggregate, arising out of or related to this Data Processing Agreement, whether in contract, tort or under any other theory of liability, is subject to the applicable limitation of liability section of the Services Agreement, and any reference in such section to the liability of a party means the aggregate liability of that party and all of its affiliates under the Services Agreement and this Data Processing Agreement together. This Data Processing Agreement represents the complete agreement concerning the subject matter hereof. The Parties may amend this Agreement, from time to time by mutual agreement of both Parties, and subject to compliance with any required obligations under applicable privacy laws (i.e., to inform the applicable authority where required). This Agreement shall be governed by and construed under the laws stipulated in the Services Agreement, without reference to principles and laws relating to the conflict of laws. The competent courts of the law stipulated in the Services Agreement shall have the exclusive jurisdiction with respect to any dispute and action arising under or in relation to this Data Processing Agreement. If Data Processor makes a material change to this Data Processing Agreement, which it may do from time to time, then Data Processor will post the updated Data Processing Agreement to its website. Data Controller is responsible for checking for any change to this Data Processing Agreement. Continued use of the Services after a change has been posted constitutes Data Controller’s acceptance of any new or modified Data Processing Agreement.
EXHIBIT 1 TO DATA PROCESSING AGREEMENT
TECHNICAL AND ORGANIZATIONAL MEASURES
Description of the technical and organizational security measures implemented by Data Processor according to Sec. 5 of the Data Processing Agreement:
Last Revised: June 6, 2019
Introduction
We, at Bringg Delivery Technologies Ltd. and its affiliates (“Bringg”, “us” or “we”), respect the security and protection of the information and data shared with us by our users and customers and their end users and customers (collectively “Users”, or “you”).
Bringg utilizes advanced tools, security procedures and engineering practices to store in a secure fashion, and protect against accidental or unlawful destruction or loss, or unauthorized disclosure or access, all User confidential or sensitive information (“User Information”) that is collected by us as part of the operation of the services of our websites and mobile applications (the “Services”).
Bringg implements a cloud-based SaaS model, currently with the use of the cloud solutions offered by Amazon Web Services (“AWS”) and Google Cloud Platform (“GCP”). By using AWS and GCP we are able to leverage the high performance, durability, scalability, availability and security of the AWS and GCP infrastructures and procedures in the provision of our Services. All User Information collected by us as part of the operation of the Services is stored in a database owned by AWS and/or GCP and controlled by us (the “Database”).
Our security procedures and practices are implemented in accordance with all applicable data protection laws, are appropriate to the nature of the information collected and are aligned with industry best practices for the management, transport, and storage of User Information. We have achieved accredited certification to ISO 27001, demonstrating that our organization has defined and put in place best-practice information security processes.
Without limiting the foregoing, we ensure that the following systems and procedures are in place:
1.Physical and Environmental Security
- The Database is located in an advanced secured data storage facility.
- Physical access is strictly controlled both at the perimeter and at building entrance points by professional security staff utilizing video surveillance, intrusion detection systems, and other electronic means. Authorized staff must pass two-factor authentication a minimum of two times to access data storage floors. All visitors and contractors are required to present identification and are signed in and continually escorted by authorized staff.
- Automatic fire detection and suppression equipment is installed to reduce risk. The fire detection system utilizes smoke detection sensors in all data center environments, mechanical and electrical infrastructure spaces, chiller rooms and generator equipment rooms.
- Data storage facility electrical power systems are designed to be fully redundant and maintainable without impact to operations, 24 hours a day, and seven days a week. Uninterruptible Power Supply (UPS) units provide back-up power in the event of an electrical failure for critical and essential loads in the facility. Data storage facilities use generators to provide back-up power for the entire facility.
- Data storage facilities are conditioned to maintain atmospheric conditions at optimal level in order to maintain a constant operating temperature for servers and other hardware, which prevents overheating and reduces the possibility of service outages. Personnel and systems monitor and control temperature and humidity at appropriate levels.
- When a storage device has reached the end of its useful life, procedures include a decommissioning process that is designed to prevent the Database or any User Information contained therein from being exposed to unauthorized individuals.
2. Business Continuity
- The infrastructure of the data storage facilities used to host the Database has a high level of availability and provides a resilient IT architecture. Such infrastructure is designed to tolerate system or hardware failures with minimal User impact.
3. Network Security
- The Database is protected by an effective network security, to control both inbound and outbound data transport, including proper monitoring of Bringg network components to detect unauthorized access.
- The Database is protected by network devices, including firewall and other boundary devices, in order to monitor and control communications at the external boundary of the network and at key internal boundaries within the network. These boundary devices employ rule sets, access control lists, and configurations to enforce the flow of User Information to or from the Database.
- Access control lists, or traffic flow policies, are established on each managed interface, which manage and enforce the flow of User Information traffic.
- Access to the Database may only be made through a limited number of access points. These access points allow secure HTTP access (HTTPS), which establishes a secure communication session with the Database.
- All User Information transmitted to or from the Database is transmitted using strong industry standard cryptography and security protocols, such as HTTP or HTTPS using Transport Layer Security (TLS 1.2 or higher).
- All User Information transmitted to or from the Database and kept in the Database is protected by a minimum of 128-bit AES encryption.
- All User Information is logically segmented or encrypted such that data may be produced for a single User only, without inadvertently accessing other User’s data.
4.Network Monitoring and Protection
- The network on which User Information is transmitted to or from the Database is constantly monitored by a wide variety of automated monitoring systems, which are designed to detect unusual or unauthorized activities and conditions at communication points.
- These tools monitor server and network usage, port scanning activities, application usage, and unauthorized intrusion attempts and set custom performance metrics thresholds for unusual activity.
- We implement Network Intrusion Detection or Prevention Systems (NIDS/NIPS) to monitor traffic of User Information to or from the Database.
- Security monitoring tools help identify, and where applicable initiate a response process against or prevent, several types of denial of service (DoS) attacks, including distributed, flooding, and software/logic attacks and also against other traditional network security issues such as Distributed Denial Of Service (DDoS) Attacks, Man in the Middle (MITM) Attacks, IP Spoofing, Port Scanning and Packet Sniffing.
- We review the security of the Services on a periodic basis including testing for common vulnerabilities such as for the malicious activities mentioned above and also including uninformed outsider testing and informed insider testing.
- All security issues that are identified shall be addressed within an appropriate timeframe.
5.Organizational Security
- Access to the Database is strictly limited to the minimum number of Bringg personnel who need to access the Database in order to facilitate provision of the Services by Bringg.
- Only authorized staff can grant, modify or revoke access to the Database.
- We apply internal security policies and procedures, which define Bringg personnel roles and their privileges, how access to the Database is granted, changed and terminated, addresses appropriate segregation of duties, and defines the logging/monitoring requirements and mechanisms.
- We implement internal security policies and procedures required to classify sensitive information assets and clarify security responsibilities.
- Our development team utilizes secure coding techniques and best practices, focused around the OWASP Top Ten. Developers are formally trained in SDL (Secure Development lifecycle) practices annually by the Security Engineering team.
- We implement a security awareness program to train Bringg personnel about their security obligations. This program includes training about data classification obligations; physical security controls; security practices and security incident reporting.
- We have clearly defined roles and responsibilities for our personnel. We conduct appropriate screening before hiring any personnel who may have access to the Database or User Information.
- We ensure that User Information contained in the Database cannot be read, copied, modified or deleted by any Bringg personnel without proper authorization, for the purpose of facilitating provision of Services.
- We insure that our hosting service provider or we conduct, on at least a yearly basis, an SSAE-16 SOC 2 audit, by an authorized auditor and/or inspector. Such audit shall include the facilities on which the Database is stored and the applicable network systems.
6.Account Security
- When a User subscribes to use our Services it is required to create one or more user, administrator or “super-user” accounts, each providing differed functions made available by the Services.
- We utilize a variety of tools and features to keep your accounts safe from unauthorized disclosure or use.
- To help ensure that only authorized Users can login and access their accounts and, we use several types of credentials for authentication, including a unique user identification and passwords.
- You specify the password when you first create the account, and you can change it at any time. Passwords may contain text, numeric figures and special characters, so we encourage you to create a strong password that cannot be easily guessed.
- Because credentials passwords can be misused if they fall into the wrong hands, we encourage you to save them in a safe place.
7.Security Breach
- Bringg shall provide you with written notice upon discovery or notification of any actual or suspected unauthorized use of or access to your User Information contained in the Database (each a “Security Breach”). All information provided you regarding the Security Breach shall be deemed Bringg Confidential Information.
- Such notice shall be made as promptly as practicable and in any event within seventy-two (72) hours (or earlier if required by applicable law) from the time such Security Breach becomes known to Bringg.
- We shall fully investigate and take all reasonable steps to identify, prevent and mitigate the effects of any Security Breach and to eliminate or contain the exposure of any User Information.
- We will, as promptly as reasonable, provide to you a description of the incident involving a Security Breach, including identifying the portions of your User Information accessed and the identity of any effected individuals in the Database.
- We will conduct any reasonable recovery necessary to remediate the impact of any Security Breach.
8.Third Party Service Providers
Bringg transfers data to third party service providers which provide certain supporting services for us, including, currently, Amazon AWS (for cloud computing services, which servers are located within the EU for EU data subjects), Google cloud (for cloud computing services, which servers are located within the EU for EU data subjects), Mandrill (for emailing services, including marketing mailing list directed, inter alia, to the website Users and customers), Google Maps (for location services, which are provided mainly to a customer’s end users and the drivers), Google Analytics (for analytics), Salesforce (for CRM), Groove (for CRM), Twilio (for SMS and voice services, such as in order to send SMS for a customer’s end user regarding the delivery of their goods) and Vonage/Nexmo (for VOIP services, such as in order to send SMS for a customer’s end user regarding the delivery of their goods). Additional third party service providers may be listed in Bringg’s privacy policy made available online, which may be updated from time to time. All of these third party service providers meet or exceed our own security measures.
9.Cloud Data Security Example – AWS
We have already described the details of how Bringg secures its resources, so we should now talk about how security in the cloud is slightly different than security for on premises data centers. When you move computer systems and data to the cloud, security responsibilities become shared between Bringg and the cloud service provider. To use AWS (Amazon Web Services) as an example, AWS is responsible for securing the underlying infrastructure that supports the cloud, and Bringg is responsible for anything we put on the cloud or connect to the cloud. This shared security responsibility model reduces the operational burden in many ways and improves our default security posture.
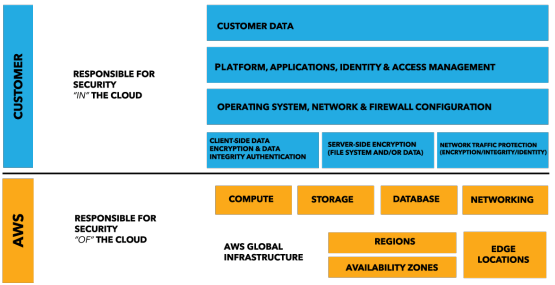
AWS operates the global cloud infrastructure that Bringg uses to provision a variety of basic computing resources such as processing and storage. The AWS global infrastructure includes the facilities, network, hardware, and operational software (e.g., host OS, virtualization software, etc.) that support the provisioning and use of these resources. The AWS global infrastructure is designed and managed according to security best practices as well as a variety of security compliance standards.
The IT infrastructure that AWS provides to its customers is designed and managed in alignment with security best practices and a variety of IT security standards, including:
- SOC 1/SSAE 16/ISAE 3402 (formerly SAS 70)
- SOC 2
- SOC 3
- FISMA, DIACAP, and FedRAMP
- DOD CSM Levels 1-5
- PCI DSS Level 1
- ISO 9001 / ISO 27001
- ITAR
- FIPS 140-2
- MTCS Level 3
Access Control of Processing Areas
Bringg implements suitable measures in order to prevent unauthorized persons from gaining access to the data processing equipment (namely telephones, database and application servers and related hardware) where the personal data are processed or used. AWS’s data centers are state of the art, utilizing innovative architectural and engineering approaches. Amazon has many years of experience in designing, constructing, and operating large-scale data centers. This experience has been applied to the AWS platform and infrastructure. AWS data centers are housed in nondescript facilities. Physical access is strictly controlled both at the perimeter and at building ingress points by professional security staff utilizing video surveillance, intrusion detection systems, and other electronic means. Authorized staff must pass two-factor authentication a minimum of two times to access data center floors. All visitors and contractors are required to present identification and are signed in and continually escorted by authorized staff.
A.Access Control to Data Processing Systems
Bringg implements suitable measures to prevent its data processing systems from being used by unauthorized persons. AWS has implemented a world-class network infrastructure that is carefully monitored and managed. Network devices, including firewall and other boundary devices, are in place to monitor and control communications at the external boundary of the network and at key internal boundaries within the network. These boundary devices employ rule sets, access control lists (ACL), and configurations to enforce the flow of information to specific information system services. ACLs, or traffic flow policies, are established on each managed interface, which manage and enforce the flow of traffic. ACL policies are approved by Amazon Information Security. These policies are automatically pushed using AWS’s ACL- Manage tool, to help ensure these managed interfaces enforce the most up-to-date ACLs. AWS has strategically placed a limited number of access points to the cloud to allow for a more comprehensive monitoring of inbound and outbound communications and network traffic. These customer access points are called API endpoints, and they allow secure HTTP access (HTTPS), which allows you to establish a secure communication session with your storage or compute instances within AWS. To help ensure that only authorized users and processes access Bringg’s AWS Account and resources, AWS uses several types of credentials for authentication. outlined in further detail in the next section.
B.Access Control to Use Specific Areas of Data Processing Systems
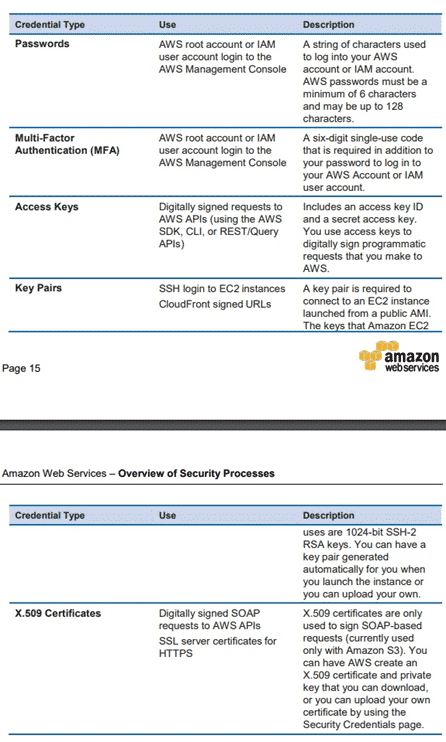
Bringg commits that the persons entitled to use its data processing systems are only able to access the data within the scope and to the extent covered by their respective access permission (authorization) and that personal data cannot be read, copied or modified or removed without authorization. (AWS developers and administrators on the corporate network who need to access AWS cloud components in order to maintain them must explicitly request access through the AWS ticketing system. All requests are reviewed and approved by the applicable service owner. Approved AWS personnel then connect to the AWS network through a bastion host that restricts access to network devices and other cloud components, logging all activity for security review. Access to bastion hosts require SSH public- key authentication for all user accounts on the host.) To help ensure that only authorized users and processes access Bringg’s AWS Account and resources, AWS uses several types of credentials for authentication. The following table highlights the various AWS credentials and their uses
C.Transmission Control
Bringg implements suitable measures to prevent the personal data from being read, copied, altered or deleted by unauthorized parties during the transmission thereof or during the transport of the data media. This is accomplished by using of state-of-the-art firewall and encryption technologies to protect the gateways and pipelines through which the data travels.
D.Input Control
Bringg implements suitable measures to ensure that it is possible to check and establish whether and by whom personal data have been input into data processing systems or removed. This is accomplished by:
1. An authorization policy for the input of data into memory, as well as for the reading, alteration and deletion of stored data;
2. Authentication of the authorized personnel; and
3. Protective measures for the data input into memory, as well as for the reading, alteration and deletion of stored data; and
4. Electronic recording of entries and logs of configuration changes and logins
E.Availability Control
Bringg implements suitable measures to ensure that personal data are protected from accidental destruction or loss and the ability to restore the availability and access to personal data in a timely manner in the event of a physical or technical incident. Amazon’s infrastructure has a high level of availability and provides customers the features to deploy a resilient IT architecture. AWS has designed its systems to tolerate system or hardware failures with minimal customer impact. Data center Business Continuity Management at AWS is under the direction of the Amazon Infrastructure Group. Data centers are built in clusters in various global regions. All data centers are online and serving customers; no data center is “cold.” In case of failure, automated processes move customer data traffic away from the affected area. Core applications are deployed in an N+1 configuration, so that in the event of a data center failure, there is sufficient capacity to enable traffic to be loadbalanced to the remaining sites. AWS provides you with the flexibility to place instances and store data within multiple geographic regions as well as across multiple availability zones within each region. Each availability zone is designed as an independent failure zone. This means that availability zones are physically separated within a typical metropolitan region and are located in lower risk flood plains (specific flood zone categorization varies by Region). In addition to discrete uninterruptable power supply (UPS) and onsite backup generation facilities, they are each fed via different grids from independent utilities to further reduce single points of failure. Availability zones are all redundantly connected to multiple tier-1 transit providers. The Amazon Incident Management team employs industry-standard diagnostic procedures to drive resolution during business-impacting events. Staff operators provide 24x7x365 coverage to detect incidents and to manage the impact and resolution.